Onion routing is a technique used in technology to enhance online anonymity by encrypting data multiple times and routing it through a series of network nodes called relays. Each relay peels away a single layer of encryption, much like an onion, revealing only the next destination in the path without accessing the original data. This layered encryption ensures that no single point in the network can identify both the sender and the receiver, significantly improving privacy. The Tor network is a prominent example of onion routing applied in practice. It operates by routing internet traffic through a worldwide volunteer overlay network, making it difficult to trace user activity. Data packets in the Tor network are encrypted in layers and passed through at least three relays, each decrypting one layer to maintain anonymity and protect against surveillance or traffic analysis.
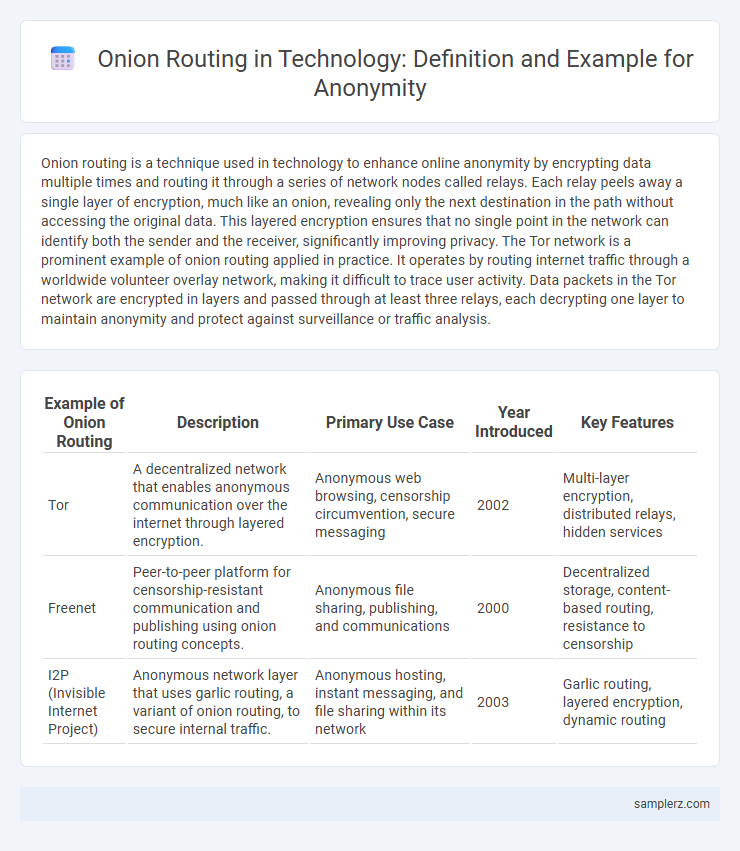
Table of Comparison
| Example of Onion Routing | Description | Primary Use Case | Year Introduced | Key Features |
|---|---|---|---|---|
| Tor | A decentralized network that enables anonymous communication over the internet through layered encryption. | Anonymous web browsing, censorship circumvention, secure messaging | 2002 | Multi-layer encryption, distributed relays, hidden services |
| Freenet | Peer-to-peer platform for censorship-resistant communication and publishing using onion routing concepts. | Anonymous file sharing, publishing, and communications | 2000 | Decentralized storage, content-based routing, resistance to censorship |
| I2P (Invisible Internet Project) | Anonymous network layer that uses garlic routing, a variant of onion routing, to secure internal traffic. | Anonymous hosting, instant messaging, and file sharing within its network | 2003 | Garlic routing, layered encryption, dynamic routing |
Introduction to Onion Routing in Anonymity
Onion routing is a privacy-enhancing technology that enables anonymous communication over a computer network by encrypting data in multiple layers. Each layer is decrypted by a successive node in the network, obscuring the origin, destination, and contents of the message. This method is widely implemented in networks like Tor, providing robust anonymity for users against traffic analysis and surveillance.
How Onion Routing Enhances Online Privacy
Onion routing enhances online privacy by encrypting data in multiple layers, ensuring that each relay node only knows its immediate predecessor and successor, which prevents any single point from tracing the entire communication path. This multi-layered encryption masks users' IP addresses and routing information, making it difficult for adversaries to link data packets to the original sender or recipient. Technologies like Tor implement onion routing to provide anonymous web browsing and protect against traffic analysis and surveillance.
Real-World Example: Tor Network and Anonymity
The Tor network uses onion routing to provide users with secure and anonymous internet access by encrypting data through multiple volunteer-operated servers called relays. Each relay peels away a single layer of encryption, preventing any single point from identifying both the origin and destination of the data. This multilayered encryption enables protection against traffic analysis, ensuring user privacy in sensitive communications and circumvention of censorship.
Core Components of Onion Routing Protocols
Onion routing protocols rely on core components such as layered encryption, which encapsulates messages in multiple encryption layers that are decrypted sequentially by intermediate nodes, ensuring anonymity and data integrity. The protocol employs routing nodes, called onion routers, which pass encrypted messages without revealing source or destination information. Hidden services use rendezvous points within the onion routing network to enable private communication without exposing either party's location.
Step-by-Step Data Flow in Onion Routing
Onion routing anonymizes data by encrypting messages in multiple layers, each decrypted sequentially by intermediate nodes called relays. The source node encrypts the message with several layers corresponding to each relay's public key, ensuring only the intended relay can access its layer. As data passes through each relay, a layer of encryption is removed, revealing routing instructions and forwarding the message until it reaches the destination, preserving anonymity and preventing tracking.
Case Study: Whistleblowing Platforms Using Onion Routing
Whistleblowing platforms like SecureDrop leverage onion routing to protect the anonymity of sources by encrypting data across multiple nodes, preventing traceability and interception. These platforms use the Tor network to route communications through layered encryption, ensuring that the origin of the submission remains undisclosed to outsiders. The adoption of onion routing in whistleblowing enhances security for journalists and activists by safeguarding sensitive information against surveillance and cyber threats.
Comparative Analysis: Onion Routing vs. VPNs
Onion routing encrypts internet traffic through multiple nodes, providing layered anonymity that makes tracing user activity extremely difficult compared to VPNs, which route traffic through a single server and rely on the provider's trustworthiness. Onion routing, exemplified by the Tor network, offers superior resistance to surveillance and traffic analysis attacks, whereas VPNs can be vulnerable to data logging and centralized point failures. This comparative analysis highlights that for enhanced privacy and decentralized security, onion routing outperforms traditional VPN solutions.
Notable Applications Leveraging Onion Routing
Tor (The Onion Router) remains the most prominent example of onion routing, providing anonymous web browsing and communication by encrypting data in multiple layers across volunteer-operated servers. I2P (Invisible Internet Project) leverages onion routing for secure and anonymous peer-to-peer communication within a decentralized network. Freenet utilizes onion routing principles to facilitate censorship-resistant publishing and file sharing, ensuring users' privacy and freedom of expression.
Challenges and Limitations in Onion Routing
Onion routing, a cornerstone of privacy technologies like Tor, faces significant challenges such as latency issues due to multiple encryption layers and relay hops, which can degrade user experience and browsing speeds. Limitations include vulnerability to correlation attacks where adversaries monitor entry and exit nodes to deanonymize users, and the dependency on volunteer-run nodes that may vary in trustworthiness and performance. Scalability concerns also arise as increasing user numbers strain the network, potentially leading to congestion and reduced effectiveness in maintaining anonymity.
The Future of Onion Routing in Anonymous Communication
Onion routing is evolving with advancements in quantum-resistant encryption and decentralized network architectures, enhancing anonymous communication resilience. Emerging protocols integrate multi-layered encryption with blockchain technology to prevent data correlation attacks and improve user privacy. Future implementations promise increased scalability and reduced latency, making anonymous browsing and secure messaging more accessible globally.
example of onion routing in anonymity Infographic
 samplerz.com
samplerz.com