Cache poisoning in web infrastructure occurs when an attacker inserts malicious data into a cache, causing users to receive corrupted or fraudulent content. This exploit targets caching systems like Content Delivery Networks (CDNs) or proxy servers by manipulating HTTP headers or DNS responses to alter cached entries. For instance, an attacker might inject false DNS records into a DNS resolver cache, redirecting users to malicious websites without their knowledge. Such attacks compromise data integrity and security, leading to phishing, malware distribution, or information theft. Web servers and CDN providers implement cache validation techniques, such as cache-control headers and DNSSEC, to defend against cache poisoning. Monitoring cache entries and validating data sources remain critical to maintaining the reliability of web infrastructure against these threats.
Table of Comparison
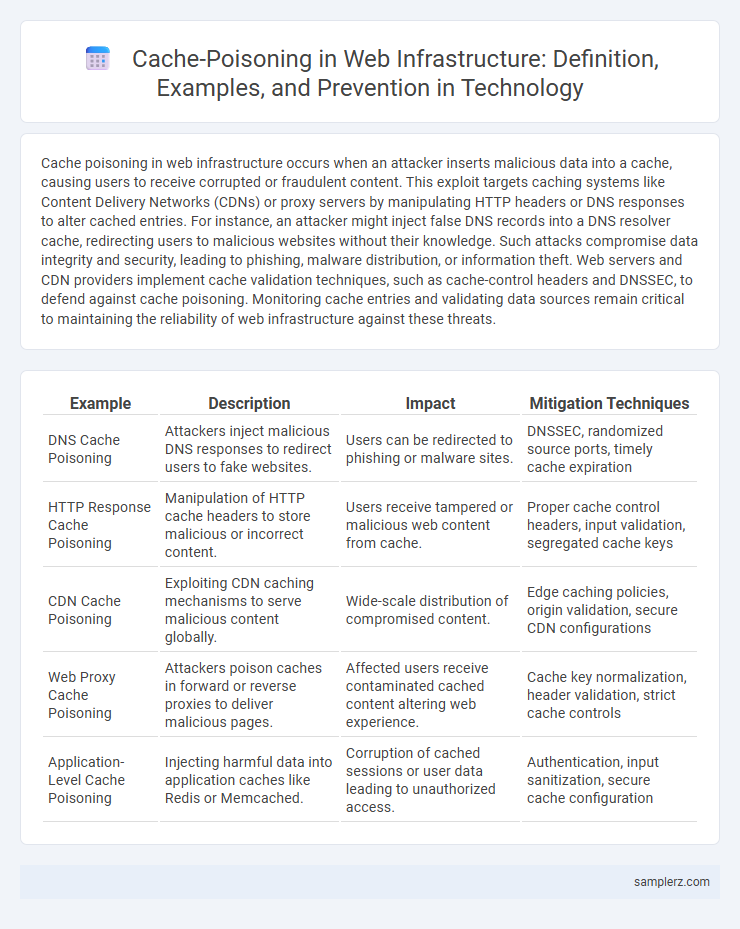
| Example | Description | Impact | Mitigation Techniques |
|---|---|---|---|
| DNS Cache Poisoning | Attackers inject malicious DNS responses to redirect users to fake websites. | Users can be redirected to phishing or malware sites. | DNSSEC, randomized source ports, timely cache expiration |
| HTTP Response Cache Poisoning | Manipulation of HTTP cache headers to store malicious or incorrect content. | Users receive tampered or malicious web content from cache. | Proper cache control headers, input validation, segregated cache keys |
| CDN Cache Poisoning | Exploiting CDN caching mechanisms to serve malicious content globally. | Wide-scale distribution of compromised content. | Edge caching policies, origin validation, secure CDN configurations |
| Web Proxy Cache Poisoning | Attackers poison caches in forward or reverse proxies to deliver malicious pages. | Affected users receive contaminated cached content altering web experience. | Cache key normalization, header validation, strict cache controls |
| Application-Level Cache Poisoning | Injecting harmful data into application caches like Redis or Memcached. | Corruption of cached sessions or user data leading to unauthorized access. | Authentication, input sanitization, secure cache configuration |
Real-World Incidents: Cache-Poisoning Attacks on Major Websites
Cache-poisoning attacks have compromised major websites like Baidu and Cloudflare, where malicious actors injected harmful content into cached web pages, leading to widespread misinformation and security breaches. In 2019, Baidu's DNS cache was poisoned, redirecting millions of users to fake domains designed to harvest sensitive data. Cloudflare experienced a similar attack exploiting vulnerabilities in its reverse proxy cache, demonstrating the critical need for robust cache validation and security protocols in web infrastructure.
How Cache-Poisoning Disrupted Web Content Delivery Systems
Cache-poisoning attacks manipulate cached web content by injecting malicious data into a web cache, causing users to receive false or harmful information instead of legitimate content. This disruption in web content delivery systems leads to widespread misinformation, degraded user experience, and increased vulnerability to malware distribution. DNS cache poisoning and HTTP header manipulation are common techniques exploited to infiltrate caching layers within Content Delivery Networks (CDNs) and reverse proxies.
Case Study: Manipulated CDN Caches Leading to Data Leaks
A notable example of cache poisoning in web infrastructure involves manipulated CDN caches that resulted in sensitive data leaks. Attackers exploited vulnerabilities in the cache key generation process, causing CDNs to serve improperly cached content from authenticated sessions to unauthorized users. This incident highlights the critical need for secure cache validation and strict control over cacheable content in distributed networks.
Exploiting HTTP Response Headers: Cache-Poisoning in Action
Cache-poisoning occurs when an attacker manipulates HTTP response headers to inject malicious content into a web cache, leading users to receive altered or harmful data instead of legitimate responses. By exploiting headers such as Cache-Control or Vary, attackers cause caching servers to store and serve poisoned responses that compromise web integrity and user security. This technique undermines trust in cached content, potentially enabling cross-site scripting (XSS), session hijacking, or delivering outdated or malicious scripts to unsuspecting users.
DNS Cache-Poisoning Impacting Web Traffic Routing
DNS cache poisoning attacks manipulate DNS resolver caches by injecting false address records, redirecting users to malicious websites instead of intended destinations. This compromised routing disrupts web traffic, enabling attackers to intercept sensitive data, deploy phishing schemes, and spread malware. Effective mitigation requires implementing DNSSEC, regularly updating DNS software, and monitoring cache behavior to prevent unauthorized data injection.
Cross-Site Scripting (XSS) Amplified by Cache-Poisoning
Cache-poisoning in web infrastructure occurs when an attacker injects malicious scripts through Cross-Site Scripting (XSS), which then get stored in shared caches, amplifying the attack's impact across multiple users. This technique allows the attacker to serve manipulated content from cache servers, leading to widespread distribution of malicious payloads without repeated injections. Exploiting vulnerabilities in cache validation and sanitization mechanisms increases the risk of XSS-based cache-poisoning attacks in complex web environments.
Server-Side Misconfigurations and Cache-Poisoning Vulnerabilities
Server-side misconfigurations such as improper cache-control headers or failing to segment cached content by user-specific parameters create cache-poisoning vulnerabilities in web infrastructure. Attackers exploit these flaws by injecting malicious responses into shared caches, causing poisoned content to be served to multiple users. Examples include HTTP header manipulation and ambiguous URL normalization triggering cache collisions and widespread data corruption.
Bypassing Authentication via Cache-Poisoned HTTP Responses
Cache-poisoning attacks in web infrastructure exploit vulnerabilities by injecting malicious HTTP responses that bypass authentication mechanisms, allowing unauthorized access to protected resources. Attackers manipulate cache entries to serve forged authentication tokens or session data, undermining user identity verification processes. This technique compromises web application security by exploiting HTTP cache directives and flawed validation protocols.
Real-World Example: Poisoned Caches Serving Malicious Content
Cache poisoning occurs when attackers manipulate cached data in web infrastructure, causing users to receive malicious content instead of legitimate resources. A notable example is the 2017 attack on major content delivery networks (CDNs), where poisoned caches served malware-laden scripts to millions of users, exploiting DNS cache vulnerabilities. This compromised the integrity of web content delivery and highlighted the critical need for stringent cache validation and security protocols.
Lessons Learned from Historical Cache-Poisoning Breaches
Historical cache-poisoning breaches, such as the notorious 2019 Cloudflare incident, revealed critical vulnerabilities in Content Delivery Network (CDN) edge caching mechanisms that allowed injection of malicious content. Detailed analysis showed that improper validation of HTTP request headers and inadequate cache key segregation facilitated unauthorized content caching, resulting in widespread user exposure to phishing attacks and data theft. These events emphasized the necessity for robust cache key management, strict input sanitization, and continuous security audits to mitigate cache-poisoning risks in web infrastructure.
example of cache-poisoning in web infrastructure Infographic
 samplerz.com
samplerz.com