Physically Unclonable Functions (PUFs) provide a unique hardware-based authentication method by leveraging inherent manufacturing variations in integrated circuits. One prominent example of PUF in authentication is SRAM PUF, which derives a device-specific fingerprint from the startup state of SRAM memory cells. This fingerprint acts as a secure cryptographic key, allowing systems to verify device identity without storing secrets externally. Another practical implementation involves Ring Oscillator PUFs, which utilize frequency variations among ring oscillators fabricated on the same chip. These frequency differences generate unique device signatures essential for secure authentication protocols. PUF-based solutions enhance protection against cloning and counterfeiting in Internet of Things (IoT) devices and secure element modules.
Table of Comparison
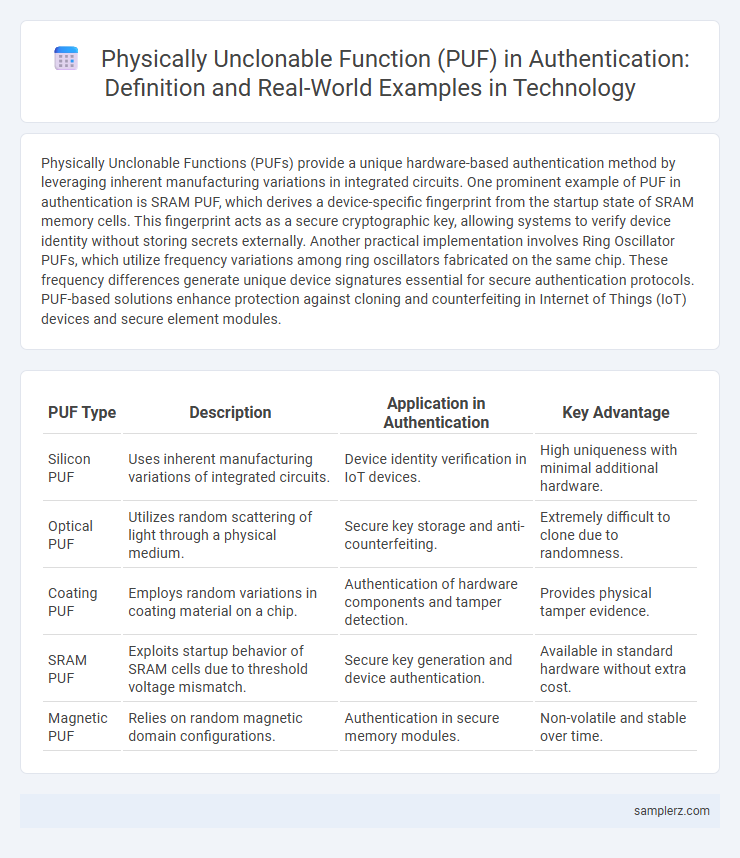
| PUF Type | Description | Application in Authentication | Key Advantage |
|---|---|---|---|
| Silicon PUF | Uses inherent manufacturing variations of integrated circuits. | Device identity verification in IoT devices. | High uniqueness with minimal additional hardware. |
| Optical PUF | Utilizes random scattering of light through a physical medium. | Secure key storage and anti-counterfeiting. | Extremely difficult to clone due to randomness. |
| Coating PUF | Employs random variations in coating material on a chip. | Authentication of hardware components and tamper detection. | Provides physical tamper evidence. |
| SRAM PUF | Exploits startup behavior of SRAM cells due to threshold voltage mismatch. | Secure key generation and device authentication. | Available in standard hardware without extra cost. |
| Magnetic PUF | Relies on random magnetic domain configurations. | Authentication in secure memory modules. | Non-volatile and stable over time. |
Introduction to Physically Unclonable Functions in Authentication
Physically Unclonable Functions (PUFs) leverage inherent manufacturing variations in semiconductor devices to generate unique, tamper-resistant hardware fingerprints essential for secure authentication. By extracting device-specific responses from these microscopic differences, PUFs provide a robust, hardware-based root of trust that resists cloning and counterfeiting in Internet of Things (IoT) devices, smart cards, and secure key storage. This technology enhances cryptographic protocols by enabling secure key generation and device identification without storing sensitive information, reducing vulnerability to physical and side-channel attacks.
Silicon PUFs: Enhancing Chip Security
Silicon PUFs exploit intrinsic manufacturing variations to generate unique identifiers for each chip, ensuring robust hardware authentication. These physical fingerprints are nearly impossible to replicate, providing high resistance against cloning and counterfeiting attacks. Integration of Silicon PUFs in secure devices significantly enhances chip security by enabling tamper-evident protection and cryptographic key generation.
SRAM PUFs for Device Identification
SRAM PUFs leverage the intrinsic manufacturing variations in SRAM cells to generate unique, device-specific identifiers used for secure authentication. These physically unclonable functions enable robust device identification by extracting stable, reproducible fingerprints from power-up SRAM states without storing secret keys. Their application in hardware security enhances resistance against cloning and counterfeiting in embedded systems and IoT devices.
Ring Oscillator PUFs in IoT Authentication
Ring Oscillator PUFs leverage inherent manufacturing variations in integrated circuits to generate unique, unclonable responses for device authentication. In IoT applications, these PUFs provide lightweight security by enabling secure key generation and device identification without storing secret keys, reducing vulnerability to physical attacks. The rapid frequency variations of ring oscillators ensure robust and reliable authentication even in resource-constrained IoT environments.
Arbiter PUFs: Securing Embedded Systems
Arbiter PUFs leverage the inherent manufacturing variability in integrated circuits to generate unique, unclonable responses for device authentication, making them ideal for securing embedded systems. Their delay-based challenge-response mechanism provides robust protection against cloning and physical attacks by utilizing path delay differences induced by process variations. This technology enhances security in IoT devices, smartcards, and hardware tokens by enabling tamper-evident authentication without requiring stored secret keys.
Optical PUFs for Document Verification
Optical Physically Unclonable Functions (PUFs) utilize unique light scattering patterns from intrinsic microstructures in materials to enable robust document authentication. By capturing these complex optical fingerprints with specialized imaging devices, Optical PUFs create tamper-evident, non-reproducible security features that significantly enhance anti-counterfeiting measures. This technology is widely applied in passports, ID cards, and certificates to ensure document integrity and prevent forgery.
Coating PUFs in Anti-Counterfeiting
Coating PUFs in anti-counterfeiting leverage unique microscopic surface patterns formed during the coating process, which are practically impossible to replicate. These physical unclonable functions generate distinct optical or electrical signatures used for authentication in high-value products and electronic components. The intrinsic randomness of coating microstructures enhances security by providing a robust, tamper-evident method for verifying genuine goods.
Memory-based PUFs for Secure Boot Processes
Memory-based Physically Unclonable Functions (PUFs) leverage unique variations in memory cells, such as SRAM or DRAM, to generate device-specific cryptographic keys for secure boot processes. These PUFs enable robust authentication by ensuring that only genuine hardware initiates the boot sequence, preventing unauthorized code execution. Their intrinsic uniqueness and resistance to cloning significantly enhance hardware security in embedded systems and IoT devices.
Field-Programmable Gate Array (FPGA) PUFs
Field-Programmable Gate Array (FPGA) PUFs leverage inherent physical variations in semiconductor manufacturing to generate unique device fingerprints, enabling secure authentication in hardware systems. FPGA PUFs provide robust resistance to cloning and tampering, ensuring reliable identity verification in applications such as cryptographic key generation and secure boot processes. Their adaptability and low-cost implementation make FPGA PUFs a scalable solution for enhancing device-level security in Internet of Things (IoT) and embedded environments.
PUF-Based Authentication Protocols in Practice
PUF-based authentication protocols leverage inherent manufacturing variations in integrated circuits to generate unique, tamper-resistant cryptographic keys. Practical implementations include SRAM PUFs used in IoT devices for secure device identification and FPGA-based PUFs for lightweight authentication in resource-constrained environments. These protocols enhance security by enabling unclonable device fingerprints that resist physical and machine learning attacks.
example of PUF (physically unclonable function) in authentication Infographic
 samplerz.com
samplerz.com