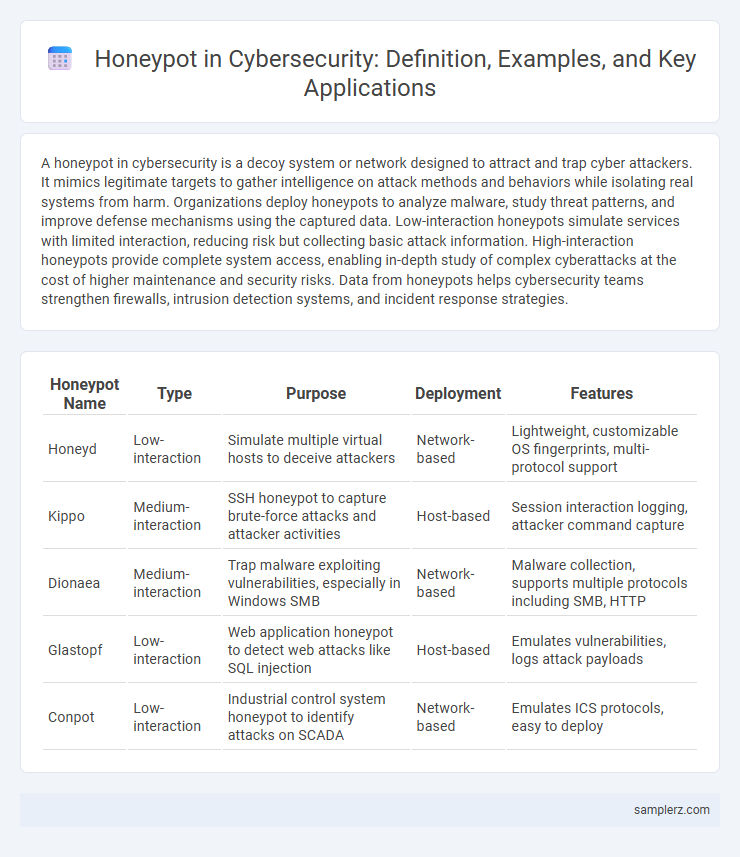
A honeypot in cybersecurity is a decoy system or network designed to attract and trap cyber attackers. It mimics legitimate targets to gather intelligence on attack methods and behaviors while isolating real systems from harm. Organizations deploy honeypots to analyze malware, study threat patterns, and improve defense mechanisms using the captured data. Low-interaction honeypots simulate services with limited interaction, reducing risk but collecting basic attack information. High-interaction honeypots provide complete system access, enabling in-depth study of complex cyberattacks at the cost of higher maintenance and security risks. Data from honeypots helps cybersecurity teams strengthen firewalls, intrusion detection systems, and incident response strategies.
Table of Comparison
| Honeypot Name | Type | Purpose | Deployment | Features |
|---|---|---|---|---|
| Honeyd | Low-interaction | Simulate multiple virtual hosts to deceive attackers | Network-based | Lightweight, customizable OS fingerprints, multi-protocol support |
| Kippo | Medium-interaction | SSH honeypot to capture brute-force attacks and attacker activities | Host-based | Session interaction logging, attacker command capture |
| Dionaea | Medium-interaction | Trap malware exploiting vulnerabilities, especially in Windows SMB | Network-based | Malware collection, supports multiple protocols including SMB, HTTP |
| Glastopf | Low-interaction | Web application honeypot to detect web attacks like SQL injection | Host-based | Emulates vulnerabilities, logs attack payloads |
| Conpot | Low-interaction | Industrial control system honeypot to identify attacks on SCADA | Network-based | Emulates ICS protocols, easy to deploy |
Real-World Honeypot Deployment Case Studies
The U.S. Department of Energy implemented a honeypot system named "Tanner" to monitor cyber threats targeting critical infrastructure, effectively capturing malware samples and attacker techniques. Researchers at the University of Michigan deployed the Honeyd honeypot to analyze botnet activities, gathering valuable data on command-and-control server communications. The Financial Services Information Sharing and Analysis Center (FS-ISAC) launched multi-tiered honeypots to detect phishing and ransomware attacks, enhancing real-time threat intelligence for member organizations.
High-Profile Honeypot Attacks Uncovered
High-profile honeypot attacks revealed sophisticated tactics used by cybercriminals to exploit decoy systems designed for threat detection. The interaction patterns within these honeypots provided critical data to cybersecurity experts, enabling the identification of advanced persistent threats (APTs) and zero-day vulnerabilities. Analysis of these incidents has significantly improved defensive measures, highlighting the importance of honeypots in proactive cybersecurity strategies.
Types of Honeypots Used in Cybersecurity
High-interaction honeypots simulate real systems with full services, capturing detailed attacker behavior and tactics. Low-interaction honeypots emulate specific vulnerabilities or services to detect automated attacks quickly and with lower resource usage. Hybrid honeypots combine elements of both, providing a balance between detailed data collection and resource efficiency to enhance threat detection and analysis in cybersecurity.
Notable Open Source Honeypot Projects
Dionaea is a widely recognized open source honeypot designed to detect malware by emulating vulnerable services and capturing exploit attempts, especially those targeting Windows systems. Cowrie focuses on SSH and Telnet protocol emulation, effectively logging brute force attacks and unauthorized login attempts to improve intrusion detection. The Glastopf honeypot specializes in web application attacks, capturing diverse exploits against vulnerabilities like SQL injection and remote file inclusion to analyze attacker behavior.
How Financial Institutions Use Honeypots
Financial institutions deploy honeypots as decoy systems designed to attract cyber attackers and analyze their tactics, techniques, and procedures (TTPs). By monitoring these simulated environments, banks identify emerging threats such as advanced persistent threats (APTs) and zero-day exploits targeting online banking platforms. Data gathered from honeypots enhances intrusion detection systems (IDS) and informs the development of robust security protocols specific to financial transaction networks.
Honeypots in Cloud Security Environments
Honeypots in cloud security environments serve as decoy systems designed to attract and analyze malicious activities targeting cloud infrastructures. These virtual traps help detect sophisticated cyber threats by mimicking vulnerable cloud services, enabling security teams to gather critical threat intelligence and improve incident response strategies. Deployment of cloud-based honeypots enhances protection against unauthorized access, data exfiltration, and advanced persistent threats in multi-tenant environments.
Honeypots for Detecting Advanced Persistent Threats (APTs)
Honeypots designed for detecting Advanced Persistent Threats (APTs) deploy sophisticated deception techniques to mimic high-value targets, attracting stealthy attackers over extended periods. These systems collect detailed attack patterns and behaviors, providing cybersecurity teams with critical insights into APT methodologies and command-and-control infrastructures. By isolating malicious activity within controlled environments, honeypots enable early detection and mitigation of covert cyber espionage campaigns.
IoT Honeypot Examples and Lessons Learned
IoT honeypots such as the HoneyPi and Conpot simulate vulnerable smart devices and industrial control systems to attract and analyze cyberattacks targeting Internet of Things networks. These honeypots revealed common attack vectors like weak authentication, outdated firmware, and exploitation of open ports, emphasizing the necessity for enhanced device security standards and regular software updates. Lessons learned from IoT honeypot deployments underscore the importance of proactive monitoring and tailored defense strategies to mitigate risks in connected environments.
Honeypots in Industrial Control Systems (ICS)
Honeypots in Industrial Control Systems (ICS) simulate critical infrastructure environments such as SCADA networks to attract and analyze cyber threats targeting operational technology (OT) components. These ICS-specific honeypots capture attack vectors like ransomware, malware propagation, and unauthorized access attempts, providing valuable threat intelligence for preventing real-world incidents. Deploying ICS honeypots enhances situational awareness and incident response capabilities by detecting advanced persistent threats (APTs) tailored to industrial processes.
Evolution of Honeypot Technologies in Enterprise Security
Honeypot technologies in enterprise security have evolved from simple decoy systems to sophisticated, AI-driven platforms that simulate real network environments and detect advanced persistent threats. Modern honeypots integrate machine learning algorithms to analyze attacker behavior in real-time, improving threat intelligence and response strategies. Enterprises leverage these adaptive honeypots to enhance intrusion detection systems, reduce false positives, and proactively secure critical infrastructure against evolving cyber threats.
example of honeypot in cybersecurity Infographic
 samplerz.com
samplerz.com