A honeypot in network security is a decoy system designed to attract cyber attackers and detect unauthorized access attempts. It mimics real network vulnerabilities, collecting valuable data on attack methods and malicious behavior without risking actual assets. Security professionals analyze this gathered information to improve threat detection systems and strengthen overall defense strategies. Honeypots vary in complexity from simple traps that log attacker IP addresses to sophisticated environments that simulate entire networks. They help identify emerging threats by monitoring attacker techniques and tools in real-time. Organizations deploying honeypots gain insights into attacker profiles and tactics, enabling proactive responses to cyber threats before they impact critical systems.
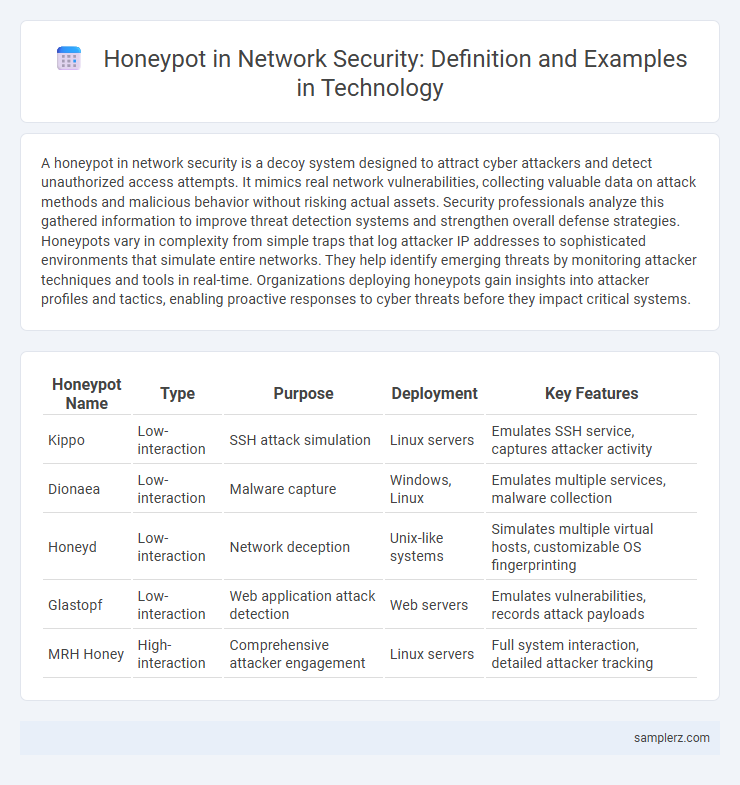
Table of Comparison
| Honeypot Name | Type | Purpose | Deployment | Key Features |
|---|---|---|---|---|
| Kippo | Low-interaction | SSH attack simulation | Linux servers | Emulates SSH service, captures attacker activity |
| Dionaea | Low-interaction | Malware capture | Windows, Linux | Emulates multiple services, malware collection |
| Honeyd | Low-interaction | Network deception | Unix-like systems | Simulates multiple virtual hosts, customizable OS fingerprinting |
| Glastopf | Low-interaction | Web application attack detection | Web servers | Emulates vulnerabilities, records attack payloads |
| MRH Honey | High-interaction | Comprehensive attacker engagement | Linux servers | Full system interaction, detailed attacker tracking |
Overview of Honeypots in Network Security
Honeypots in network security serve as decoy systems designed to attract and analyze cyberattackers, enabling organizations to detect threats and gather intelligence. These traps simulate vulnerable targets, diverting malicious traffic away from critical assets while providing valuable data on attack methods and tools. Implementing honeypots enhances threat detection capabilities and supports proactive defense strategies by revealing attacker behavior and potential vulnerabilities.
Common Types of Honeypots Used in Modern Networks
Low-interaction honeypots simulate limited services to detect automated attacks with minimal risk, commonly used for early threat detection. High-interaction honeypots provide full operating systems for attackers to interact with, gathering comprehensive intelligence on attacker behavior and tactics. Distributed honeypots deploy multiple decoys across a network, enhancing visibility into complex, large-scale threat patterns and improving overall network security monitoring.
Real-World Honeypot Deployment Scenarios
Real-world honeypot deployment scenarios include financial institutions using decoy servers to detect and analyze cyber threats targeting online banking systems. Internet Service Providers implement honeypots to monitor and mitigate Distributed Denial of Service (DDoS) attacks by capturing malicious traffic patterns. Another example involves enterprise networks deploying low-interaction honeypots to identify insider threats and unauthorized lateral movement within the corporate infrastructure.
High-Interaction Honeypot Examples
High-interaction honeypots like Honeyd and Cowrie simulate entire operating systems and services, providing in-depth insights into attacker behaviors and tactics. Dionaea captures malware by emulating vulnerable services, allowing security teams to analyze real attack payloads in controlled environments. These honeypots generate rich threat intelligence by engaging attackers fully, aiding in the development of robust cybersecurity defenses.
Low-Interaction Honeypot Implementations
Low-interaction honeypots, such as Honeyd and Kippo, simulate specific network services to detect unauthorized access with minimal resource usage. These implementations capture attacker techniques and patterns without fully compromising system integrity, making them ideal for large-scale deployment and early threat detection. By emulating common protocols like SSH and HTTP, they efficiently gather valuable threat intelligence while reducing the risk of exploitation.
Popular Open-Source Honeypot Projects
Popular open-source honeypot projects in network security include Honeyd, Dionaea, and Cowrie, which simulate vulnerable systems to attract and analyze cyberattacks. Honeyd allows the creation of virtual hosts with customizable network services, effectively deceiving attackers and capturing their methods. Dionaea specializes in malware collection by emulating vulnerable protocols, while Cowrie focuses on SSH and Telnet honeypot interactions, providing detailed threat intelligence for intrusion detection.
Case Studies: Successful Honeypot Applications
The University of Michigan deployed a high-interaction honeypot that successfully detected and analyzed Advanced Persistent Threats (APTs), providing critical insights into attacker behavior and malware propagation. The Honeynet Project's global network of honeypots captured zero-day exploits and phishing attacks, enabling rapid development of defense mechanisms in real-world scenarios. Google's Project Honeypot identified spambots and malicious IP addresses, significantly reducing spam and improving email security across millions of users worldwide.
Practical Tools for Honeypot Construction
Cowrie is a widely-used honeypot designed to emulate SSH and Telnet services, capturing attackers' login attempts and commands for analysis. Dionaea specializes in detecting malware by mimicking vulnerable services like SMB, FTP, and HTTP to lure and capture malware samples. Honeyd enables the creation of virtual hosts on a network, allowing the simulation of various operating systems to deceive attackers and gather intelligence on their scanning and exploitation techniques.
Notable Attacks Detected by Honeypot Systems
Honeypot systems have effectively detected notable attacks such as the Mirai botnet that exploited IoT devices to launch massive DDoS attacks in 2016. Another significant incident includes the Stuxnet worm, which targeted industrial control systems, revealing critical vulnerabilities through honeypot environments. These detections provide valuable threat intelligence for improving network defense mechanisms and anticipating emerging cyber threats.
Best Practices for Honeypot Integration in Networks
Deploying low-interaction honeypots, such as Cowrie, enables organizations to simulate common network services and capture attacker behaviors without risking critical assets. Best practices for honeypot integration include isolating the honeypot in a segmented VLAN to prevent lateral movement, regularly updating honeypot systems to mimic current vulnerabilities, and monitoring traffic with Security Information and Event Management (SIEM) solutions for real-time threat analysis. Effective use of honeypots also involves combining data from decoy systems with endpoint detection tools to enhance overall network threat intelligence.
example of honeypot in network security Infographic
 samplerz.com
samplerz.com